Protecting online accounts has grown more important than ever in the digital era. Data breaches, cyberattacks, and identity theft are all rather frequent; depending just on passwords is not enough to guard private data. Here, multi-factor authentication (MFA) finds application. Using MFA is a good way to improve security since it makes users check their identity by means of several elements. This all-inclusive guide shows how to apply MFA properly to guard priceless information and access online accounts.
What is Multi-Factor Authentication (MFA)?
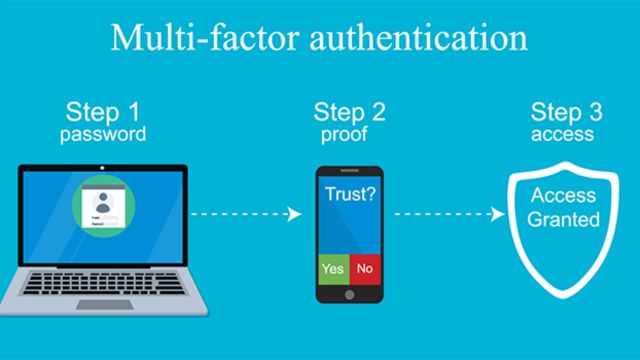
To access an account, system, or application, users of Multi- Factor Authentication (MFA) must present two or more verifying elements. MFA offers extra layers of protection to confirm the user’s identity, unlike conventional single-factor authentication (which makes just use of a password).
The most common MFA methods include:
- Something You Know: This refers to information the user knows, such as a password, PIN, or security question.
- Something You Have: This involves a physical device like a smartphone, security token, or smart card.
- Something You Are: This includes biometric data such as fingerprints, facial recognition, or voice recognition.
Combining these factors ensures that even if one method is compromised, unauthorized access is still prevented due to the additional verification layers.
Benefits of Implementing MFA
Implementing MFA offers several key benefits that significantly enhance the security of online systems and accounts:
- Enhanced Security: By requiring multiple forms of verification, MFA reduces the risk of unauthorized access. Even if a hacker obtains the password, they would still need to pass other verification steps.
- Reduced Risk of Data Breach: Data breaches often occur due to compromised credentials. MFA mitigates this risk by adding extra verification steps that are harder for attackers to bypass.
- Compliance with Regulations: Many industries, such as finance, healthcare, and government sectors, require MFA to comply with data protection regulations and security standards.
- Protection Against Phishing: MFA prevents phishing attacks by requiring a second verification step, making it difficult for attackers to use stolen credentials.
- Improved User Trust: Users are more likely to trust systems that implement robust security measures like MFA, fostering a secure online environment.
Step-by-Step Guide to Implementing MFA
To effectively implement MFA, follow these detailed steps:
1. Assess Your Current Security Framework:
Before using MFA, review your present security system. List the systems and programs that include sensitive information needing more security. For every system, ascertain their degree of security risk and give MFA implementation top priority in high-risk sectors. For instance, you should give accounts including intellectual property, personal data, or financial information top priority.
2. Choose the Appropriate MFA Methods:
Choose MFA techniques most appropriate for the demands of your company. Think through user comfort, security needed, and integration possibilities. Typical MFA approaches comprise:
- Authenticator Apps: These apps generate time-based one-time passwords (TOTPs) that users must enter during login. Examples include Google Authenticator, Microsoft Authenticator, and Authy.
- SMS and Email Codes: Temporary codes are sent to the user’s registered phone number or email address.
- Biometric Verification: Fingerprint scanning, facial recognition, or voice recognition add a layer of physical security.
- Hardware Tokens: Physical devices such as USB tokens or smart cards that generate unique authentication codes.
3. Develop a Comprehensive Implementation Plan:
Create a detailed plan that outlines how MFA will be implemented across the organization. This plan should include:
- The scope of implementation (e.g., specific systems, applications, or user groups).
- A phased rollout strategy to minimize disruptions.
- User education and training to ensure smooth adoption.
- Contingency plans for lost or stolen authentication devices.
4. Integrate MFA with Existing Systems:
Make sure the selected MFA solution can fit perfectly with current systems and applications. Configuring APIs, building up identity management systems, and allowing MFA choices in user accounts might all be part of this.
MFA can be turned on for cloud-based systems as Microsoft 365 or Google Workspace by means of the security settings of the account. Think about applying OAuth or SAML authentication mechanisms for bespoke developed systems.
5. Configure and Test MFA Settings:
Once the MFA solution is integrated, configure the settings according to the security requirements. This includes:
- Defining which authentication methods will be used.
- Setting up backup methods in case the primary method is unavailable.
- Implementing lockout policies for failed authentication attempts.
- Conducting test logins to ensure the MFA system functions as intended.
6. Educate Users and Provide Support:
User education is crucial to successful MFA implementation. Conduct training sessions to inform users about the importance of MFA, how to set it up, and how to use it effectively. Provide clear instructions for each MFA method and offer support for common issues, such as resetting authentication methods or recovering access in case of device loss.
7. Monitor and Maintain the MFA System:
Implementing MFA is not a one-time task. Continuous monitoring is necessary to identify potential vulnerabilities and address emerging threats. Regularly update the MFA system to accommodate new security protocols and user feedback. Additionally, review authentication logs to detect unusual login attempts or unauthorized access attempts.
Recommended Platforms for MFA Registration
Below are some widely used platforms where users can register and enable MFA:
- Microsoft 365:
Microsoft offers MFA through its security settings for accounts. Users can set up MFA by following the step-by-step guide provided by Microsoft at Microsoft 365 MFA Setup. - Google Account:
Google provides a secure 2-Step Verification process that can be set up via Google’s Security Checkup. Users can choose from app-based codes, SMS codes, or hardware keys. - Duo Security:
Duo Security offers a comprehensive MFA solution that supports various authentication methods. Organizations can implement MFA for applications and systems through Duo’s Setup Guide. - Authy:
Authy is a free authentication app that generates time-based OTPs and supports multiple accounts. Users can register for Authy at Authy. - Okta:
Okta provides enterprise-grade MFA solutions with biometric verification, push notifications, and hardware tokens. Setup information can be found at Okta MFA Setup.
Discover the latest updates on government schemes and digital initiatives at DigitalIndiaMIB.com. Stay informed, apply for benefits, and secure your future with verified, easy-to-understand information. Visit us today and empower yourself with the right knowledge for a better tomorrow!
FAQ
What Are Common MFA Authentication Failures?
Common MFA failures include lost devices, expired codes, or connectivity issues. Users should have backup options like recovery codes or alternate verification methods to avoid lockouts.
Can MFA Be Bypassed By Hackers?
While MFA significantly reduces risks, sophisticated attackers may exploit vulnerabilities like SIM swapping or phishing. Continuous updates and user awareness help prevent these bypass attempts.
How Does MFA Impact User Experience?
MFA may add extra steps to login but improves security. Using convenient methods like push notifications or biometrics minimizes disruption while keeping accounts safe.
Is MFA Mandatory For All Online Accounts?
MFA is recommended but not mandatory for every account. Critical services like banking and email benefit most, while less sensitive platforms may offer it as an optional security layer.
What Are The Costs Associated With MFA?
Costs vary depending on the method: authenticator apps are often free, while hardware tokens and enterprise solutions may require investment. Many free and low-cost MFA options exist.
















